What is security compliance?
Being security compliant means your IT protocols follow prevailing local and international industry standards, as well as adhere to any laws that apply in your locality.
Examples include adhering to local privacy and security of personal information laws if, for example, you record your customers’ personal and/or financial details. There are also global standards, such as the ISO/IEC 27000 family, that relate to the security of information management systems and are considered best practice.
These standards are there to help organisations keep their information assets secure. Your business could be subject to fines or worse if you don’t act to adequately protect your data assets.
SMBs are at risk
The real impact of a data security breach is economic, and felt most acutely by SMBs, which often don’t have the human and financial resources to deal with it. In fact, around 71 per cent of security breaches target small businesses and 60 per cent of small businesses who experience a cyberattack end up shutting down.
The evolving nature of cybercrime also makes IT security a challenge for smaller organisations to keep up with.
Never say 'never'
While many large-scale companies have been victims of hackers, including Yahoo, Sony and internet infrastructure company Cloudflare, when it comes to IT security, never assume your business is small enough to slip under the radar. Cybercriminals don’t discriminate.
Five-step security compliance checklist
Follow these five steps to ensure your security protocols are compliant:
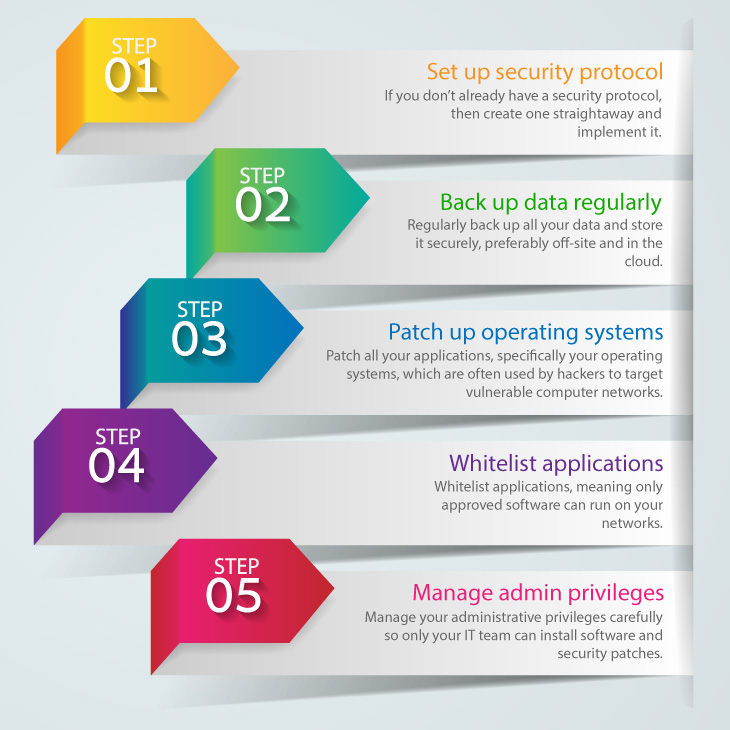
In terms of prioritising your resources, the trick is to strike a balance and focus on protecting your business against security issues that come with the most financial risk.
As a business owner, it’s your responsibility to identify threats to your organisation and take the necessary steps to ensure you’re security compliant. And think of it this way: ultimately, preventing security breaches will cost less than fixing one.



